Organizations of all sizes now routinely demand security and compliance certifications from their service providers, a trend that has led to a surge in certifications such as NIST Cybersecurity Framework, ISO 27001, SOC 2, and HIPAA. These certifications serve as the bedrock upon which data protection and brand reputation stand. The implications of choosing the right framework are profound, reverberating across industries and marketplaces.
In this deep dive into these vital cybersecurity frameworks, we offer clarity and guidance to help you make informed decisions in the pursuit of cybersecurity excellence. Whether you’re the captain of a cybersecurity team, a business unit head, or the owner of an enterprise, this guide equips you to make a difference in safeguarding your organization’s most valuable asset: its data.

What you'll find in this article
- 1 NIST Security Guidelines: The Federal Touchstone
- 2 ISO 27001: The Global Standard
- 3 SOC 2: Assurance for Service and Product Providers
- 4 HITRUST: Simplifying HIPAA Compliance
- 5 HIPAA: Safeguarding Patient Health Information
- 6 PCI-DSS: Fortifying Card Transactions
- 7 Other Standards and Frameworks: Tailored Solutions
- 8 Choosing the Path to Cybersecurity Excellence
NIST Security Guidelines: The Federal Touchstone
The National Institute of Standards and Technology (NIST) has long been a cornerstone of cybersecurity, initially designed for federal agencies and later adopted across various industries. The most prominent publication, NIST Special Publication 800-53, outlines a Risk Management Framework to select security controls for federal information systems, ensuring adherence to Federal Information Processing Standards (FIPS) 200.
While NIST CSF (Cybersecurity Framework) is a voluntary framework, organizations can choose to undergo a certification process to demonstrate their compliance with the framework. The certification process is typically conducted by a third-party auditor and involves an assessment of the organization’s cybersecurity program against the NIST CSF standards. There are several certification programs available for NIST CSF, including the Certified NIST Cybersecurity Framework Lead Implementer (CSF LI) certification and the NIST Cybersecurity Professional Foundation Certification Training.
Key Features of NIST:
- Certification: NIST can be certified, and this involves working with authorized certification bodies to add credibility to your security measures.
- Approach: NIST adopts a risk-based approach, emphasizing the identification and prioritization of risks to tailor security measures.
- Best Suited For: It was originally designed for federal agencies but has extended its reach, making it valuable for organizations seeking authoritative security best practices.
Key Tip: Engage certified NIST professionals to guide you through the certification process and assist in risk identification and mitigation.
ISO 27001: The Global Standard
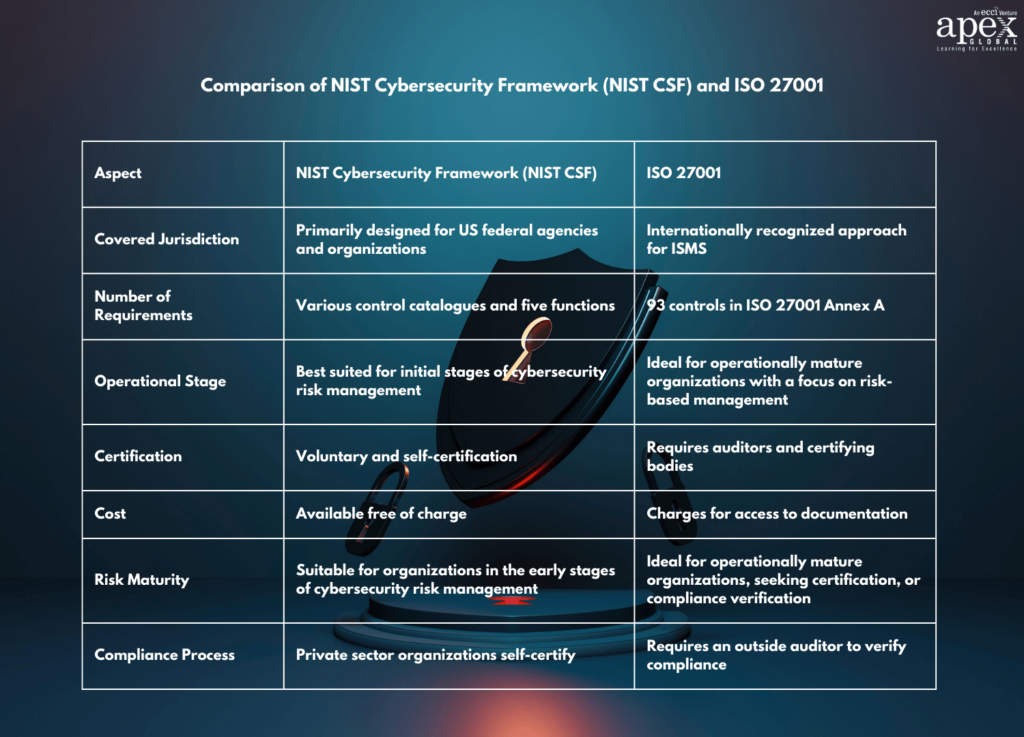
ISO/IEC 27001 is a risk-based standard with worldwide recognition. The ISO/IEC 27000 family comprises multiple standards, but ISO/IEC 27001 is the most renowned. It delineates the requirements for an Information Security Management System (ISMS) applicable to organizations of all sizes, safeguarding assets like financial information, intellectual property, and data entrusted to third parties.
Key Features of ISO 27001:
- Certification: ISO 27001 certification is achievable through authorized bodies and is a testament to your commitment to information security.
- Approach: It shares a risk-based approach similar to NIST, enabling tailored security strategies.
- Best Suited For: ISO 27001 is versatile and fits the security needs of organizations worldwide.
Key Tip: Start by reviewing ISO 27001’s requirements and then approach authorized certification bodies to initiate the certification process.
SOC 2: Assurance for Service and Product Providers
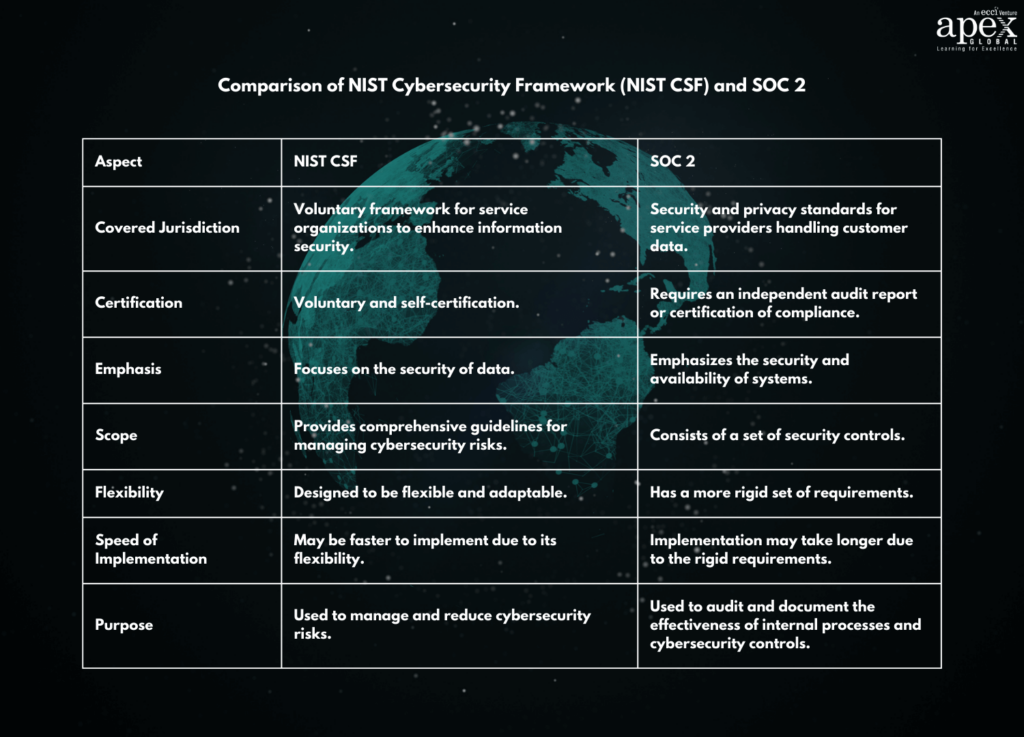
Service and product organizations in North America lean towards SOC 2 to gain client trust. SOC 2 reports evaluate security controls, following the American Institute of Certified Public Accountants’ (AICPA) Trust Services Principles. It offers assurance regarding Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Key Features of SOC 2:
- Certification: SOC 2 necessitates working with authorized Certified Public Accountant (CPA) firms, who conduct readiness assessments before certification.
- Approach: SOC 2 adopts a controls-based approach, focusing on the five Trust Services Principles.
- Best Suited For: Service and product organizations, especially those looking to secure B2B contracts, find SOC 2 certification invaluable.
Key Tip: A readiness assessment by a vendor can help you identify gaps in your security controls and procedures before engaging a CPA firm for certification.
HITRUST: Simplifying HIPAA Compliance
HITRUST, or the Health Information Trust Alliance, bridges the gap between vendors and covered entities in demonstrating compliance with HIPAA requirements. It introduces a standardized framework for securing health information, and addressing critical concerns in the healthcare sector.
Key Features of HITRUST:
- Certification: HITRUST certification is granted by the HITRUST Alliance, validating your adherence to HIPAA standards.
- Approach: As a framework for healthcare, it employs a controls-based approach, mirroring the depth of HIPAA requirements.
- Best Suited For: Healthcare organizations and entities handling protected health information (PHI) of U.S. citizens should consider HITRUST.
Key Tip: Identify gaps in your organization’s HIPAA compliance and work towards closing them, in preparation for HITRUST certification.

HIPAA: Safeguarding Patient Health Information
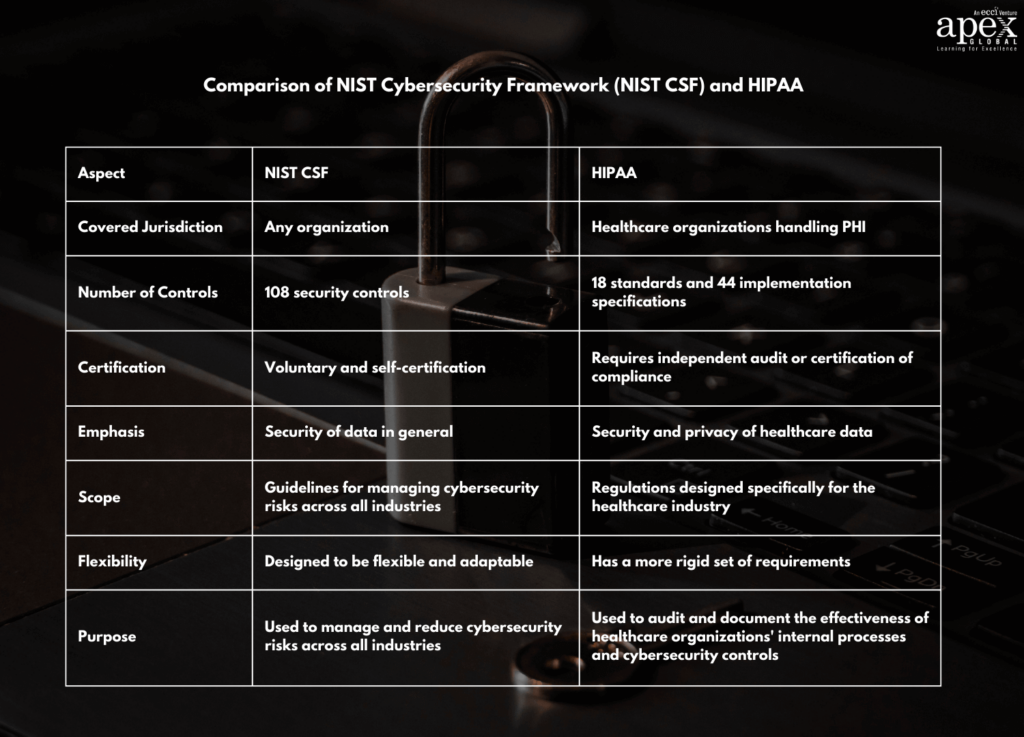
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) stands as a federal law safeguarding patient health information. Its recent updates grant more control to patients over their health data. HIPAA compliance is non-negotiable for healthcare organizations, and any entity handling PHI of U.S. citizens.
Key Features of HIPAA:
- Certification: HIPAA doesn’t have a certification process, but you can conduct self-audits or engage a third party to attest to your compliance.
- Approach: HIPAA’s controls-based approach emphasizes technical, administrative, and physical safeguards for patient health information.
- Best Suited For: HIPAA applies to healthcare organizations and any entity handling PHI of U.S. citizens – it’s the law.
Key Tip: Commence with a self-audit, and if required, enlist a third-party expert to attest to your HIPAA compliance.
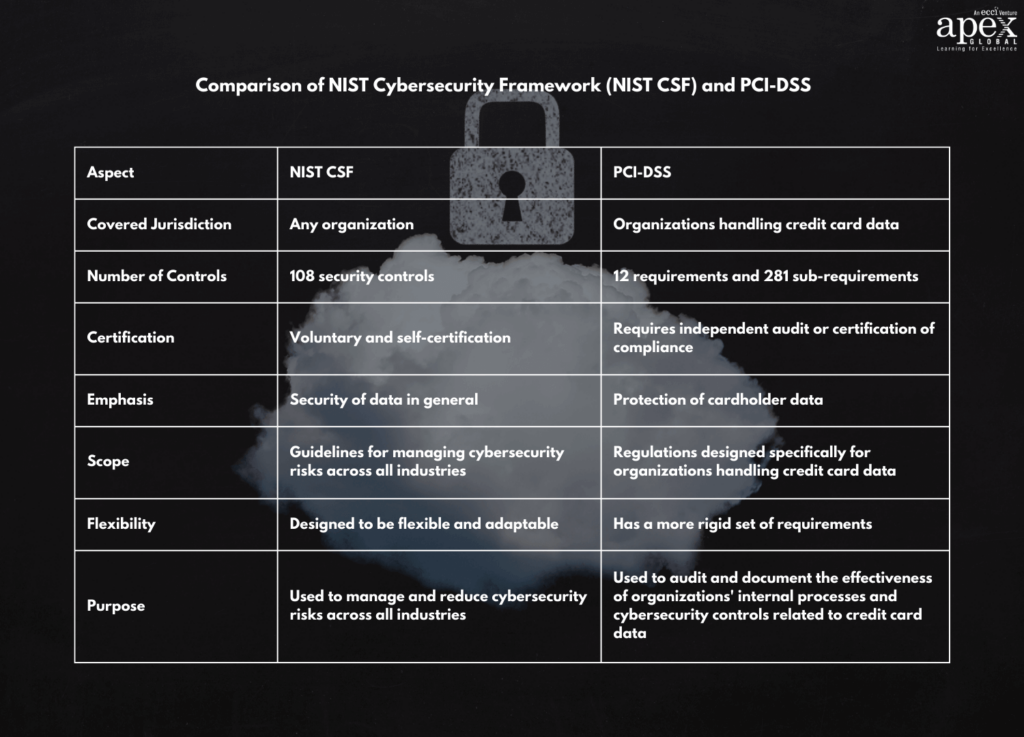
PCI-DSS: Fortifying Card Transactions
The Payment Card Industry Data Security Standard (PCI-DSS) provides comprehensive security standards for credit and debit card transactions. For organizations handling these transactions, PCI certification is imperative.
Key Features of PCI-DSS:
- Certification: Achieving PCI certification mandates collaboration with authorized vendors possessing PCI Qualified Security Assessor (QSA) certification.
- Approach: PCI-DSS revolves around controls designed to safeguard credit and debit card data against theft.
- Best Suited For: Any organization involved in credit or debit card transactions must strive for PCI certification.
Key Tip: Begin by conducting a comprehensive assessment of your current systems and procedures. Engage with an authorized vendor with QSA certification to guide you toward PCI compliance.
Other Standards and Frameworks: Tailored Solutions
In addition to these major frameworks, specialized industry-specific standards like FedRAMP, Cloud Security Alliance (CSA), and Shared Assessments offer tailored solutions to cater to various requirements. The adoption of these standards hinges on the specific needs and compliance requirements of your industry and marketplace.
Key Features of Other Standards/ Frameworks:
- Certification and Accreditation: Most industry-specific frameworks require third-party accreditation, necessitating engagement with accredited vendors or assessors.
- Best Suited For: The applicability of these standards and frameworks is contingent on your industry’s distinct requirements and the marketplace where you operate.
Key Tip: If your industry demands adherence to a specialized framework, collaborating with accredited vendors or assessors versed in your sector’s nuances is essential for successful certification.
Choosing the Path to Cybersecurity Excellence
When choosing a cybersecurity framework, you’re not merely selecting a checklist for compliance. You’re shaping the fortress that will protect your organization’s data.
APEX Global Learning offers a 2-day training program focused on Cybersecurity Posture with the NIST Framework. This program equips you with the necessary knowledge and skills to guard against cyber threats using the NIST Cybersecurity Framework. Designed for individuals and teams alike, it’s the perfect opportunity to enhance your cybersecurity posture and safeguard your organization from potentially devastating losses.
NIST Cybersecurity Framework, ISO 27001, SOC 2, and other frameworks are more than acronyms. They are the sentinels of your digital assets. By understanding their features, certification processes, and applicability, you empower yourself to lead the charge in cybersecurity excellence. Your responsibility in this interconnected digital world is significant, and the framework you choose will determine your organization’s resilience in the face of cyber adversaries.