Let’s be honest, updating to the latest ISO 27001 ISMS Standard is like getting the latest iPhone, but for your company’s cyber defense. Plus, you don’t want to be caught with your guard down when hackers come knocking on your digital door.
With cyber threats evolving and becoming more sophisticated each day, it’s crucial to stay ahead of the game and ensure your organization’s information security is up to par. The new version of the standard brings important updates and revisions to address current security challenges and align with new technological developments.
- It provides a more comprehensive approach to risk management, including updated guidance on risk assessment and treatment.
- The updated standard also places more emphasis on asset management and incorporates a more proactive approach to identifying and managing security incidents.
- It also takes into account the evolving technology landscape and provides updated guidance on cloud security and BYOD policies.
Whether you’re new to ISO 27001 or a seasoned pro, the new standards have something to offer everyone. We’ve put together a comprehensive guide where we’ll break down the ISO 27001:2022 changes and what they mean for your organization’s security posture.
Trust us, you won’t want to miss this!
What you'll find in this article
- 1 What is an ISMS?
- 2 What is ISO 27001
- 3 How can ISO 27001 help keep your data safe?
- 4 The latest update to ISO 27001 – ISO 27001:2022
- 5 ISO 27001 2013 vs. 2022 revision – What has changed?
- 6 ISO 27001:2022 Update
- 7 What are the 11 new security controls in ISO 27001:2022?
- 7.1 Security control #1: Annex.5.7 Threat intelligence
- 7.2 Security control #2: Annex.5.23 Information security Cloud services
- 7.3 Security control #3: Annex.5.30 ICT readiness for business continuity
- 7.4 Security control #4: Annex.7.4 Physical security monitoring
- 7.5 Security control #5: Annex.8.9 Configuration management
- 7.6 Security control #6: Annex.8.10 Information deletion
- 7.7 Security control #7: Annex.8.11 Data masking
- 7.8 Security control #8: Annex.8.12 Data leakage prevention
- 7.9 Security control #9: Annex.8.16 Monitoring activities
- 7.10 Security control #10: Annex.8.23 Web filtering
- 7.11 Security control #11: Annex.8.28 Secure coding
- 8 Transitioning to ISO 27001:2022 – How can organizations prepare themselves?
- 9 Final thoughts
What is an ISMS?
ISMS stands for Information Security Management System and it’s a framework designed to manage and protect sensitive company information. There are many advantages to having an ISMS in place, including protecting your organization from cyber threats, ensuring compliance with regulations, and improving overall efficiency. Not to mention, it gives your clients peace of mind knowing their data is secure.
The goal of any ISMS is to protect the confidentiality, integrity, and availability of information assets. Here’s a quick list of ISMS goals to keep in mind:
- Identify and assess information security risks
- Implement appropriate security controls
- Ensure legal, regulatory, and contractual compliance
- Continuously monitor and review the effectiveness of the ISMS
- Maintain an up-to-date incident response and business continuity plan
ISMS best practices
If you’re not already incorporating ISMS best practices in your organization, it’s about time you start! Cybersecurity threats are ever-increasing, and being ignorant of these practices can lead to catastrophic consequences for your organization. Implementing ISMS best practices helps protect your sensitive data and helps build trust with your clients. Plus, it’s always good to be one step ahead of potential cyber-attacks. So, take some time to educate yourself and your team on the importance of ISMS best practices. Trust me, your organization and clients will thank you for it!
Here’s a quick rundown of the key ISMS best practices:
- Create an information security policy
- Conduct regular risk assessments
- Train employees on information security
- Implement access controls
- Back up important data regularly
- Monitor system activity
- Regularly review and update your ISMS
Implementing ISMS
Do you want to ensure the safety and security of your organization’s sensitive data and information? The answer lies in implementing ISMS (Information Security Management System). But how do you go about doing that?
Here are 5 key points to get you started:
1. Identify key stakeholders & their responsibilities – Are you aware of the responsibilities of your organization’s stakeholders in your ISMS? It’s crucial to have everyone on the same page when it comes to information security.
2. Determine the scope & objectives of your ISMS – To protect your organization, you must identify what you need to safeguard, like employee data or confidential client information, and then define your security goals. Your objectives should align with your organization’s goals and be specific, measurable, attainable, relevant, and timely.
3. Conduct a risk assessment – This helps you identify potential vulnerabilities and threats to your company’s sensitive data, so you can take action to mitigate those risks. It’s better to be proactive than reactive when it comes to cybersecurity.
4. Establish policies, procedures & controls – If you’re looking to implement ISMS successfully in your organization, ISO 27001 and Plan Do Check Act (PDCA) can definitely help. ISO 27001 sets the standard for information security management systems, while PDCA provides a framework for continual improvement. By combining the two, you can establish, implement, maintain, and continually improve your ISMS to ensure the confidentiality, integrity, and availability of your information assets.
5. Train your employees & conduct regular reviews – Make sure that every employee is well-versed in security procedures and knows how to identify potential threats. It’s a confirmed way of ensuring that everyone plays an active role in protecting our company and its data.
What is ISO 27001
ISO 27001 is an international standard for information security management systems. It sets out requirements for establishing, implementing, maintaining and continually improving an organization’s information security management system.
So, why should you care? Because information security is important for any business that deals with sensitive information. Implementing ISO 27001 helps organizations identify and mitigate potential security risks, and ensures the confidentiality, integrity, and availability of information. Plus, it gives clients and partners confidence in your ability to protect their information.
How can ISO 27001 help keep your data safe?

Wondering how implementing ISO/IEC 27001 can benefit your organization? Here’s a list for you:
- It establishes your commitment to information security and provides reassurance to stakeholders.
- It ensures that information assets are protected against unauthorized access, modification, loss or damage.
- It helps in the prevention of cyber-attacks and reduces the risk of financial loss.
- It aids in the development of your company’s policies and procedures to ensure consistent security practices.
- It improves employee awareness and helps to build a culture of security within the organization.
By following the rigorous standards outlined in the certification process, you can ensure the confidentiality, integrity, and availability of your organization’s information. Not only does this boost your credibility and customer trust, but it can also save you from costly security breaches. Don’t underestimate the importance of cybersecurity in today’s world – get certified and protect your business.
The latest update to ISO 27001 – ISO 27001:2022
Are you keeping up with the latest updates in ISO 27001? That’s right, ISO 27001:2022 is here! This update brings some exciting changes to the standard, including improved guidance on risk assessment and an increased focus on managing outsourced processes.
There are some key changes you’ll want to know about.
First up, there’s an increased focus on risk management throughout the standard, with the Annex A controls now being tied to specific risks.
Additionally, the structure of the standard has been revised to align with other ISO management system standards, making it easier to integrate with other management systems.
And finally, there’s more emphasis on the role of top management in driving information security within organizations.
As more and more companies rely on digital technologies, the need for robust security measures has never been more important. So, if you’re responsible for managing your organization’s information security, staying up to date with these changes is critical for maintaining the security of your organization’s information assets.
Let’s explore in detail!
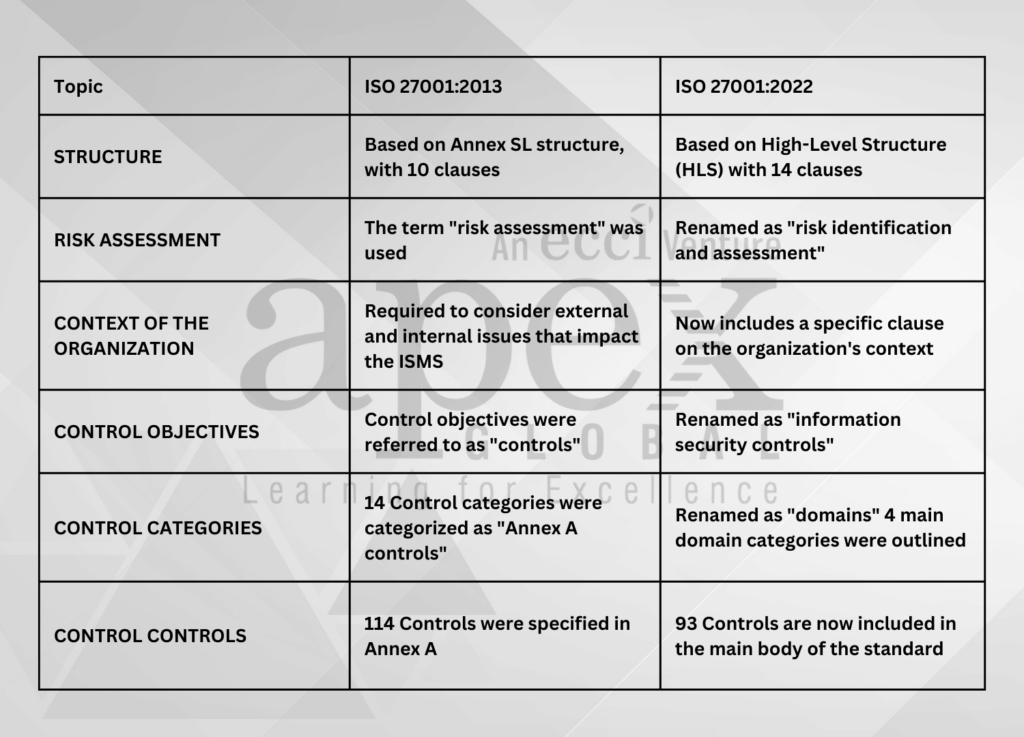
ISO 27001 2013 vs. 2022 revision – What has changed?
In the 2013 version of ISO 27001, there were 114 Annex A controls divided into 14 categories. That was quite the checklist to ensure that organizational information security is up to snuff! While it certainly brought some improvements, there were some critical challenges as well.
For one, the increased complexity of the new controls was quite overwhelming. And let’s not forget the amount of effort needed to keep up with the frequent audits and maintenance required to comply with the new requirements.
This led to the need for the next update to the ISO 27001 framework. The latest ISO 27001:2022 update has arrived and it comes packed with some impressive advantages.
ISO 27001:2022 Update
Here are some to give you an idea:
- Better alignment with modern business processes.
- Clearer guidance on information security risks and opportunities.
- Enhanced focus on information security performance.
- A strengthened emphasis on supply chain risk management.
The number of controls has decreased from 114 to 93, and they’re now grouped into four main domains. How neat is that? These changes will make navigating the system so much easier for all of us.

People domain contains 8 controls – This standard outlines the measures required to protect people from any data breaches or information leakages, from screening to education to disciplinary processes. It emphasizes the importance of confidentiality and provides businesses with guidance to keep sensitive information secure.
Organizational security domain contains 37 controls – It covers all the necessary controls for policies, management, inventory, classification, labeling, authentication, and more.
Physical domain contains 14 controls – It puts an increased focus on physical security controls, including security perimeters, equipment, storage, cabling, and monitoring, just to name a few. These controls can help protect against environmental threats and potential breaches.
Technological domain contains 34 controls – It covers everything from information access to network security, and you can ensure your data stays protected from all kinds of threats. Don’t forget to prioritize secure authentication, malware protection, and data masking – these are essential for maintaining your privacy and staying ahead of any cyber attackers.
What are the 11 new security controls in ISO 27001:2022?
Are you ready to dive into the latest changes to ISO 27001? There are 11 new security controls in the 2022 version that you need to know about. As always, ISO 27001 sets the standard for information security management, and staying up to date on the latest changes is crucial for keeping your organization secure.
Security control #1: Annex.5.7 Threat intelligence
The Annex.5.7 of ISO 27001 requires organizations to maintain up-to-date threat intelligence information and utilize it to enhance their cybersecurity posture. This includes tracking known and emerging threats, analyzing potential impacts, and proactively mitigating risks.
Security control #2: Annex.5.23 Information security Cloud services
This security control outlines information security protocols for cloud services. First, make sure you have clear policies and procedures for selecting, approving, and monitoring cloud services. Secondly, you need to document the security requirements and controls for the cloud services you use. And finally, you need to ensure that you have procedures in place to manage and monitor access to those services.
Security control #3: Annex.5.30 ICT readiness for business continuity
To comply with Annex.5.30, we need to take certain steps to ensure our ICT readiness for business continuity.
If you’re thinking about compliance, here are some steps to consider:
- Identify your critical ICT resources and assets
- Evaluate potential disruptions and their impact on your business
- Develop and implement appropriate business continuity plans
- Test your plans regularly
Security control #4: Annex.7.4 Physical security monitoring
In Annex 7.4 of the standard, you’ll find guidelines on physical security monitoring.
Here are the necessary steps to make sure your physical security is up to par:
- Conduct a risk assessment to identify potential security threats
- Establish security policies and procedures based on your assessment
- Implement security controls, including access control, CCTV, and security alarms
- Monitor and review security measures regularly to ensure they are effective and up to date
Security control #5: Annex.8.9 Configuration management
This annex outlines the steps required for configuration management compliance.
To stay ahead of the curve, here are the steps you need for Annex.8.9 compliance:
- Define your configuration items and keep them up-to-date.
- Establish configuration baselines to track changes.
- Regularly review and verify changes.
- Securely store configuration items to protect sensitive information.
Security control #6: Annex.8.10 Information deletion
Compliance with Annex.8.10 isn’t just important for regulatory purposes, but also helps safeguard your business and customer data.
So here’s a quick overview of the steps you need to take:
- Establish and maintain documented procedures for the secure disposal of information assets
- Implement tools to sanitize or destroy the information in line with those procedures
- Train your employees on how to correctly handle and dispose of information
- Periodically review and update the process to ensure ongoing compliance
Security control #7: Annex.8.11 Data masking
The Annex.8.11 gives detailed instructions for compliance about data masking in ISO 27001:2022
We’ve got you covered with some steps to get you started.
First, identify your sensitive data and assess your risks. From there, develop your masking strategies and establish policies for handling and protecting masked data. Lastly, conduct regular testing and reviews to ensure your system remains effective.
Security control #8: Annex.8.12 Data leakage prevention
Annex.8.12 Data leakage prevention in ISO 27001:2022 is all about keeping your sensitive data safe from getting into the wrong hands.
Here are some simple steps to get you on track for compliance:
- Identify what sensitive data you need to protect
- Define how to protect that data from leakage
- Implement security measures
- Regularly monitor and review those measures
Security control #9: Annex.8.16 Monitoring activities
Annex.8.16 monitoring activities in ISO 27001:2022 compliance is one of the critical aspects of the latest security management standard.
Here are some simple steps to achieve compliance with Annex.8.16:
- Define your organization’s monitoring objectives
- Determine the monitoring controls that need to be implemented
- Design the monitoring program according to the control objectives
- Execute the monitoring activities
- Record and report on the monitoring activities to senior management.
Security control #10: Annex.8.23 Web filtering
With cyber-attacks becoming increasingly common, it’s essential to keep your online presence secure, and Annex.8.23 Web Filtering in ISO 27001:2022, is just one piece of the puzzle.
To stay compliant, there are certain steps that you need to take. First, you need to define your web filtering requirements and implement them. Then, you need to review and update your policies and procedures, train your employees, and conduct regular testing to ensure that everything is working effectively.
Security control #11: Annex.8.28 Secure coding
Ensuring compliance with Annex 8.28 is essential for safeguarding your company’s data and maintaining the trust of your customers.
First off, you need to assess your current coding practices and identify any potential security gaps. Then, you can implement secure coding techniques such as input validation, output encoding, and error handling. Additionally, regular code reviews and penetration testing can help detect and prevent security vulnerabilities.
Transitioning to ISO 27001:2022 – How can organizations prepare themselves?
With the new version ISO 27001:2022, there are changes to the framework and additional security requirements. So, if you’re an organization thinking about making the transition to ISO 27001:2022, it’s essential to prepare yourselves now.
First and foremost, you’ll want to start by familiarizing yourself with the updated requirements and understanding how they differ from the previous standard. From there, it’s important to conduct an in-depth gap analysis to identify areas of improvement and prioritize the necessary changes.
Don’t forget to communicate the upcoming changes to your team and ensure everyone is on board with the transition. Consider hosting training sessions to keep everyone up-to-date and engaged throughout the process.
You can check our the ISMS practitioner course at APEX Global Learning. This has been designed specifically with such minute professional performance indicators in mind. This immersive course is aligned with ISO 27001:2022 and designed to help you establish an up-to-date ISMS body in your organization.
With the right preparation and proactive approach, the transition to ISO 27001:2022 can be a seamless and rewarding experience for your organization.
Final thoughts
As the final thoughts on this topic, we have to say that the changes made in the latest iteration are quite impressive.
With updates to risk management processes, information security controls, and even the overall structure of the standard, it’s clear that the international community is committed to strengthening information security across the board.
So, whether you’re working in IT, cybersecurity, or any other industry that deals with sensitive information, be sure to keep ISO 27001:2022 in mind. By implementing its guidelines, you’ll be taking proactive steps to keep yourself and your organization safe in today’s rapidly evolving digital landscape.


